Smart design means smart features.
Flexible system with enterprise level engineering and support for leading industry technologies.
Application Proxying
Most DDoS Protection providers only provide support for HTTP connections. With us you can protect any application (or service) that communicates using both the TCP and UDP protocols.
This means you can protect Mail (SMTP) servers, Game servers, IRC chat and even Java sockets. Our network is resilient enough for anything you can throw at it.
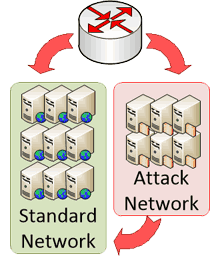
Split Network Design
Our network been designed with reliability in mind, utilizing a split-network system to split clean and attack traffic.
When a DDoS attack is detected the IPs under attack are transferred to the filtering cluster. Here traffic is scrubbed using commercial and inhouse filtering hardware to remove the attack (bad) traffic before fowarding the remaining to your backend.
Enterprise Grade Hardware
Under heavy attacks, even the most robust software firewall will collapse. We utilise the latest technology, providing protection against a wide variety of floods, including:
- TCP SYN Flood
- Comprehensive TCP and UDP Layer Flood (Saturation and Fragmentation)
- ICMP Ping (and response) flood
- HTTP Protocol (RUDY, Slowloris, etc) and Bot floods
DDoS Protection
Our DDoS protection plans come with hardware filtering. We have the latest hardware & mitigation software to filter:
- TCP SYN Flood
- Comprehensive TCP and UDP Layer Flood
- HTTP Request and DNS Query Flood
- Saturation and Bad Packet Attacks
Hardware Protection
Under large attacks even the most robust software firewall will collapse, we utilise the latest SecurePort and other filtering hardware to protect your website or service.
GRE/IPIP Tunnels
Support for GRE/IPIP tunnels for maximum compatibility and reliability. Great for game servers, with all Operating Systems supported, including Microsoft Windows.
More InformationLarge Resilient Network
We have hundreds of Gbps of network capacity from large transit providers including Tinet, Cogent, Comcast, Zayo, HE, Atrato and Level3. More than enough to provide the protection we advertise.
Application Proxying
We also provide proxying for any application that utilizes TCP or UDP to communicate. Communication is provided over a Reverse Proxy or Tunnel to your backend server. Supported applications include:
- Web Services HTTP/HTTPS/FTP
- Game Servers (e.g Minecraft and HL;DS)
- IRC (Chat)
HTTPS / SSL support
Provide HTTPs connectivity to your site without the extra load, have us take care of it for you. You can provide your own certificate, or we can generate one for you as needed.
HTTP/2 protocol supported
We support the latest HTTP/2 protocol for for fast web communication. This protocol is targeted at reducing page load time by up to 50%. Secure and enabled by default for all HTTPS ports.
More InformationCaching
We allow pages to be cached on our server. This means they are only fetch once for a long period of time. This decreases bandwidth usage and speeds up page load through reducing latency for your visitors. This is optimum for the serving of static files that rarely change.
HTTP Keep Alive
Our backend proxy only connects to your server a set number of times, reusing those connections for all connected clients.This reduces the latency of creating a connection for every client. We also keep clients connected after they have finished their requests for this purpose, while allowing the backend connection to be used by other clients.
GZIP Compression
All data compressed with GZIP compression for minimal bandwidth consumption and maximum user performance. GZIP is supported on all modern browsers (newer than Internet Explorer 4), and enabled for all browsers greater than Internet Explorer 6 (or similar). GZIP allows for file size reductions of approximately 10 times on most HTML content pages and has similar ratios for CSS and Javascript resources.
Split networks
When under attack specific IPs are re-routed through hardened switches and additional hardware to ensure reliability and to protect the clean network. This network employs other protection methods such as tighter UDP and ICMP restrictions.